Windows Server 2022
Microsoft’s operating system for server computers including Active Directory, DNS Server, DHCP Server and Group Policy

Downloads
Change hostname
Rename-Computer -NewName Server1 -PassThru
Set time zone
Set-TimeZone "Central Europe Standard Time”
Set time and date
Set-Date -Date "05/17/2022 08:12"
Scan the system for any device hardware changes
List devices
Install device driver
pnputil -i -a D:\NetKVM\2k22\amd64\*
read more…
Change server core shell
Set-ItemProperty -Path 'HKLM:\Software\Microsoft\Windows NT\CurrentVersion\WinLogon' -Name Shell -Value 'PowerShell.exe'
Enable PowerShell script execution
Set-ExecutionPolicy RemoteSigned
Set PowerShell default working directory
notepad $PSHOME\Profile.ps1
read more…
Disable automatic updates
Set-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate\AU -Name AUOptions -Value 1
Enable install and manage updates via PowerShell
Install-PackageProvider -Name NuGet -Force
Install-Module -Name PSWindowsUpdate -Force
Create PowerShell updates inbound firewall rules
Download and install all available updates locally from Windows Update servers
Install-WindowsUpdate -MicrosoftUpdate -AcceptAll -AutoReboot
Restart local computer
Stop (shut down) local computer
Update remote computers
Get-WindowsUpdate -verbose -computer core,client1,server1 -AcceptAll -Install -AutoReboot
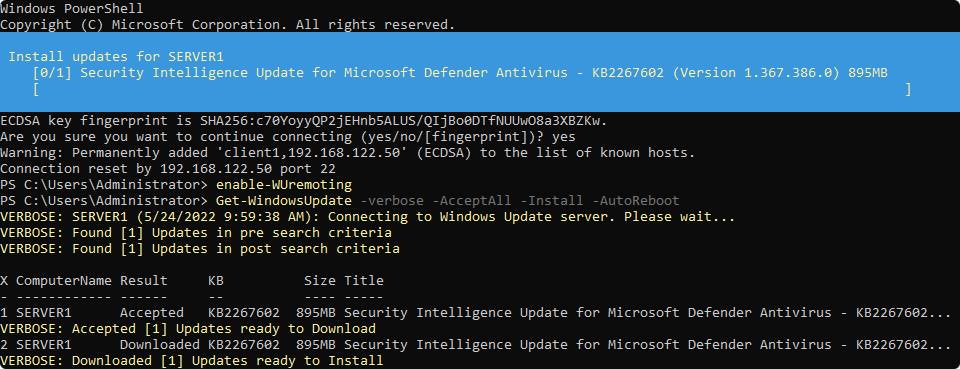
Restart remote computers
Restart-Computer -ComputerName core,client1,server1 -Force
Stop (shut down) remote computers
Stop-Computer -ComputerName core,client1,server1 -Force
Enable download optional features directly from windows update
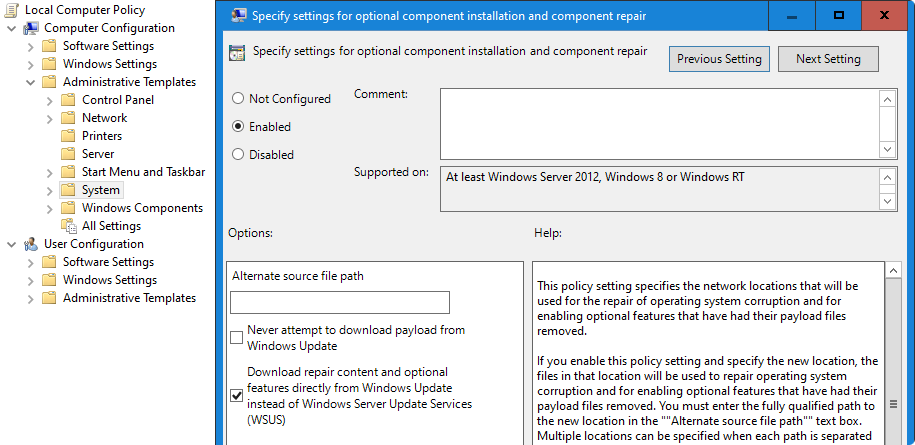
Set-ItemProperty -Path HKLM:\Software\Microsoft\Windows\CurrentVersion\Policies\Servicing -Name RepairContentServerSource -Value 2
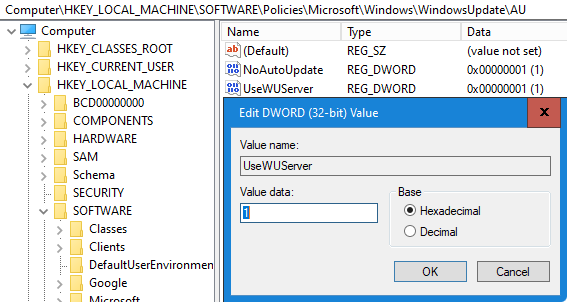
Set-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate\AU -Name UseWUServer -Value 1
Feature on Demand (FOD)
Microsoft offers a special package which allows you to install some graphical tools and snap-ins on Windows Core Server.
Install-WindowsFeature -Name Failover-Clustering -IncludeManagementTools
Add-WindowsCapability -Online -Name ServerCore.AppCompatibility
Install Feature on Demand from mounted ISO image
Add-WindowsCapability -Online -Name ServerCore.AppCompatibility -Source D:\LanguagesAndOptionalFeatures\ -LimitAccess
Server Configuration sconfig
Microsoft Management Console mmc
Event Viewer eventvwr
Performance Monitor perfmon
Resource Monitor resmon
Device Manager devmgmt
File Explorer explorer
Windows PowerShell powershell_ise
Disk Management diskmgmt
Failover Cluster Manager clusdmin
Hyper-V Manager virtmgmt
Task Scheduler taskschd
read more…
Check network profile
Set network profile from Public to Private
Set-NetConnectionProfile -InterfaceIndex 3 -NetworkCategory Private
Check network settings
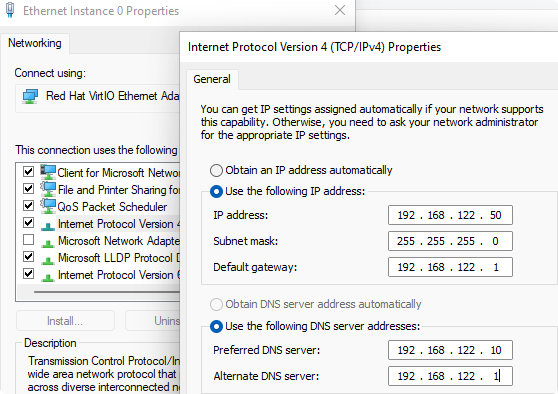
Set manual IP Address
New-NetIPaddress -InterfaceIndex 3 -IPAddress 192.168.122.20 -PrefixLength 24 -DefaultGateway 192.168.122.1
Set Active Directory domain server as DNS server
Set-DNSClientServerAddress -InterfaceIndex 3 -ServerAddresses 192.168.122.10,192.168.122.1
Note
Reset IP address
Set-DnsClientServerAddress -InterfaceIndex 3 -ResetServerAddresses
Return to getting an IP address from DHCP Server
Set-NetIPInterface -InterfaceIndex 3 -Dhcp Enabled
Set TrustedHosts
Set-item wsman:\localhost\client\TrustedHosts -value *
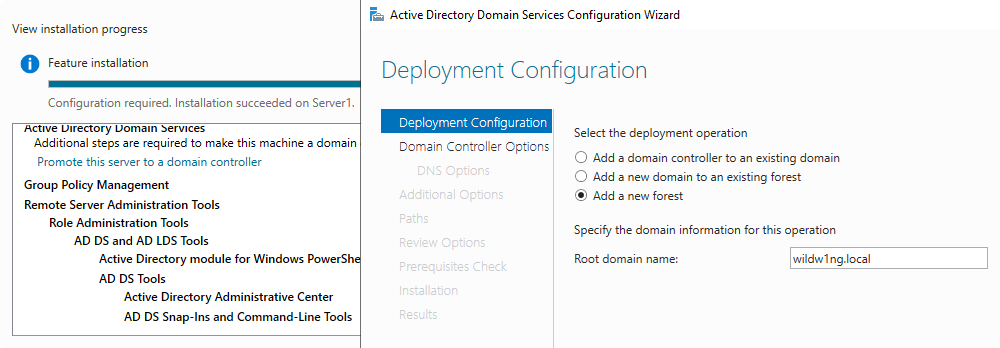
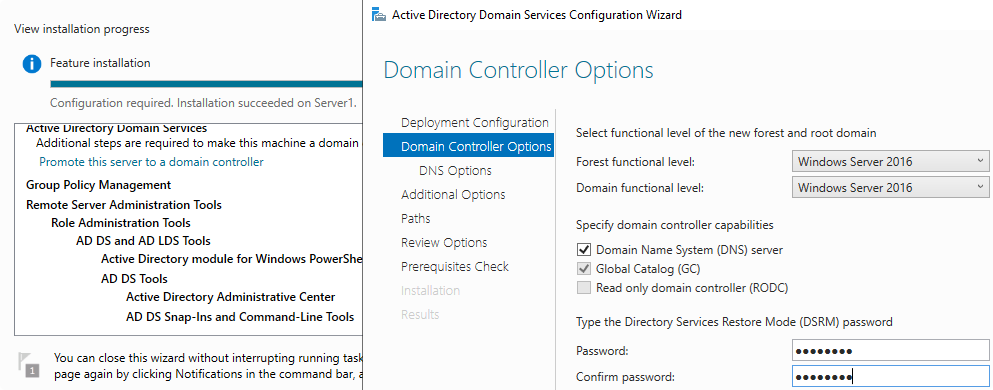
Enable Active Directory domain services
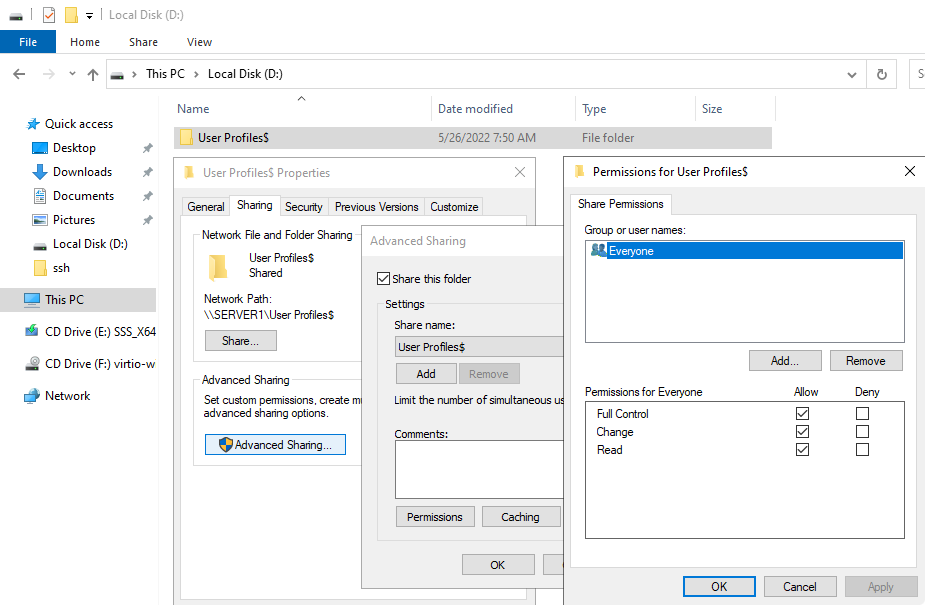
Create and share Roaming user profiles directory
Create Roaming user profiles template
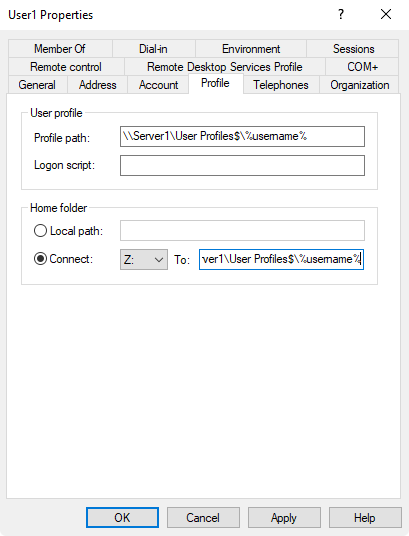 Profile path
Profile path \\Server1\User Profiles$\%username%
read more…
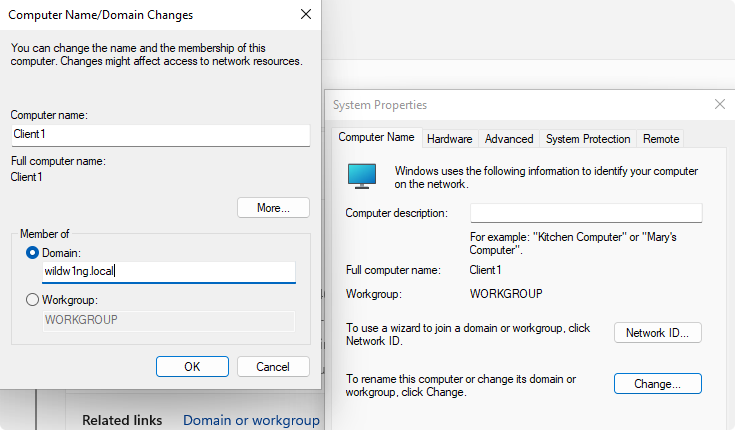
Join on-premises Active Directory domain
Tip
Enable ping response on Server Core
Sconfig.exe > option 4) Remote management > option 3) Enable server response to ping
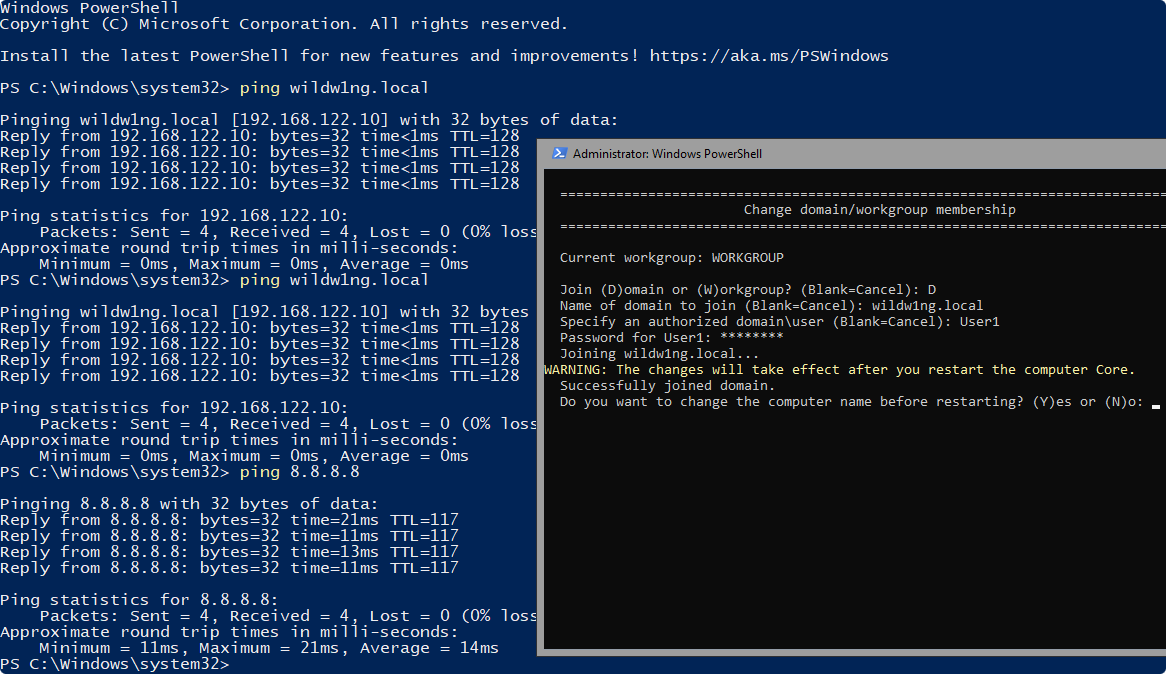
Add-Computer -DomainName "wildw1ng.local" -Restart
Add second Domain Controller to an existing domain
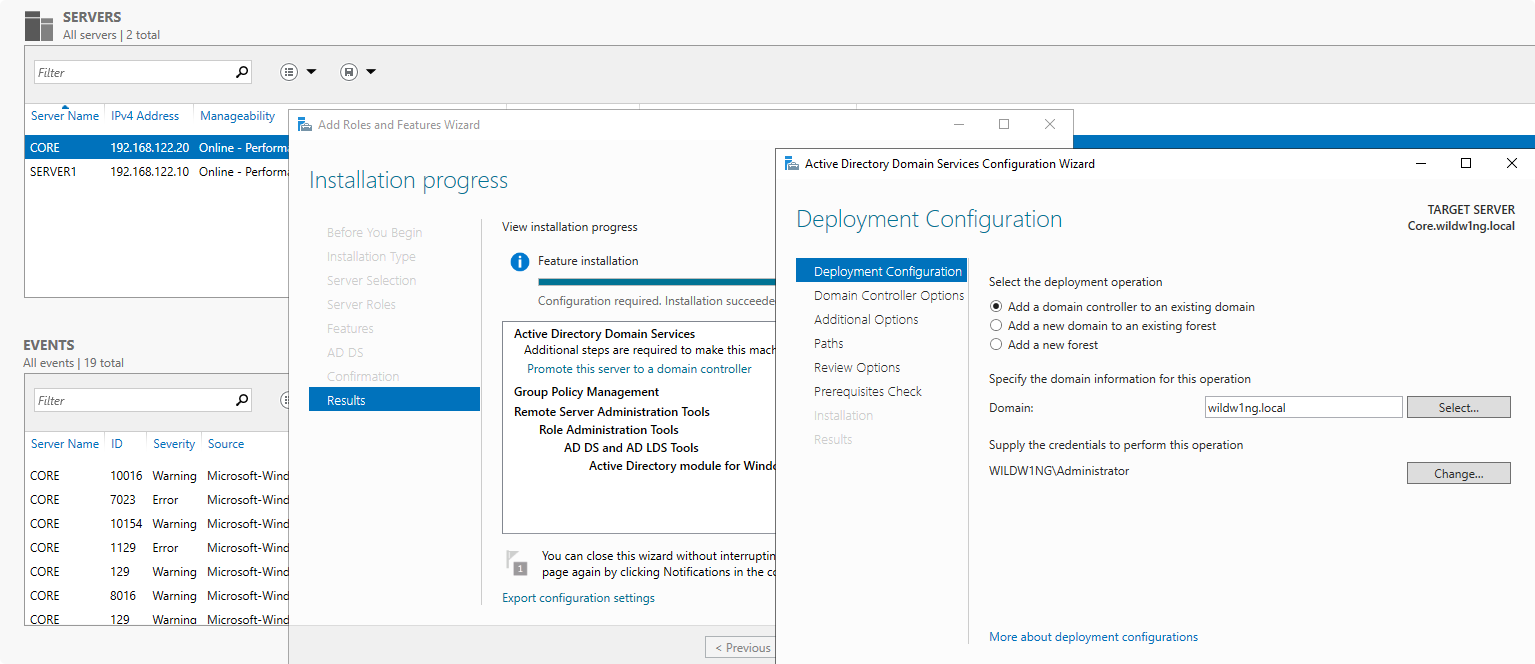
Disable network adapter
Disable-NetAdapter -Name “Ethernet0”
Enable network adapter
Enable-NetAdapter -Name “Ethernet0”
Disable IPv6 support for your network adapter
Disable-NetAdapterBinding -Name "Ethernet0" -ComponentID ms_tcpip6
Enable IPv6 support for your network adapter
Enable-NetAdapterBinding -Name "Ethernet0" -ComponentID ms_tcpip6
Check the status of IPv6 support for your network adapter
Get-NetAdapterBinding -ComponentID ms_tcpip6
netsh Winhttp set proxy SERVERNAME:PORT
Enable Windows Defender Firewall for all profiles
Set-NetFirewallProfile -Profile Domain,Public,Private -Enabled True
Note
Completely disable Windows Firewall
Get-NetFirewallProfile | Set-NetFirewallProfile -Enabled False
Check available OpenSSH packages
Get-WindowsCapability -Online | ? Name -like 'OpenSSH*'
Install OpenSSH client
Add-WindowsCapability -Online -Name OpenSSH.Client
Install OpenSSH server
Add-WindowsCapability -Online -Name OpenSSH.Server
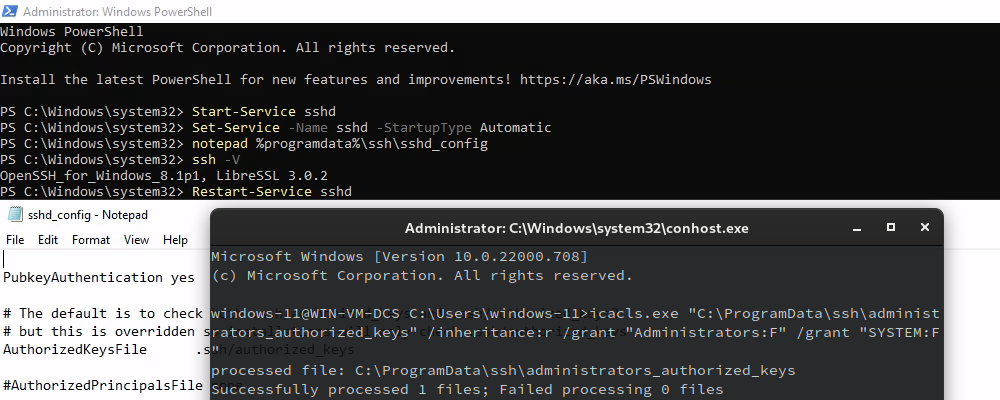
Start the sshd service
Set-Service -Name sshd -StartupType Automatic
Allow incoming connections to TCP port 22 in the Windows Defender Firewall
New-NetFirewallRule -Name sshd -DisplayName 'OpenSSH-Server-In-TCP' -Enabled True -Direction Inbound -Protocol TCP -Action Allow -LocalPort 22
notepad verify-ssh-firewall.ps1
if (!(Get-NetFirewallRule -Name "OpenSSH-Server-In-TCP" -ErrorAction SilentlyContinue | Select-Object Name, Enabled)) {
Write-Output "Firewall Rule 'OpenSSH-Server-In-TCP' does not exist, creating it..."
New-NetFirewallRule -Name 'OpenSSH-Server-In-TCP' -DisplayName 'OpenSSH Server (sshd)' -Enabled True -Direction Inbound -Protocol TCP -Action Allow -LocalPort 22
} else {
Write-Output "Firewall rule 'OpenSSH-Server-In-TCP' has been created and exists."
}
.\verify-ssh-firewall.ps1
Tip
Run PowerShell cli instead of cmd.exe shell when logging in via SSH
New-ItemProperty -Path "HKLM:\SOFTWARE\OpenSSH" -Name DefaultShell -Value "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -PropertyType String -Force
Connect to OpenSSH Server
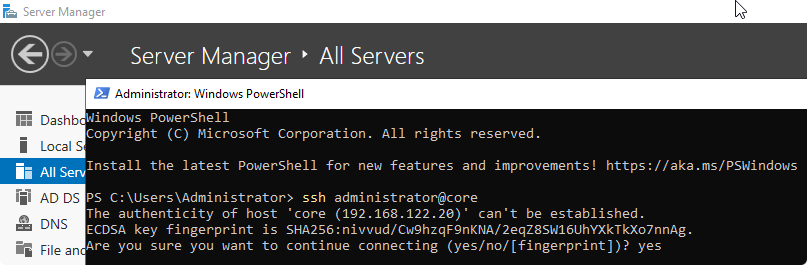
System-wide configuration file at %programdata%\ssh\ssh_config
Public key authentication
Copy and rename ~/.ssh/id_rsa.pub from linux
to windows server %programdata%\ssh\administrators_authorized_keys
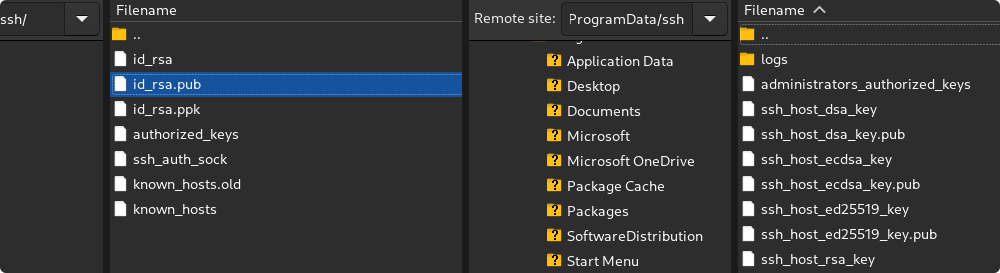
Update access control list (ACL)
icacls.exe "C:\ProgramData\ssh\administrators_authorized_keys" /inheritance:r /grant "Administrators:F" /grant "SYSTEM:F"
Open SSH Server (sshd) reads configuration data from %programdata%\ssh\sshd_config by default
notepad %programdata%\ssh\sshd_config
PubkeyAuthentication yes
PasswordAuthentication no
read more…
Enable remote access via RDP
cscript C:\Windows\System32\Scregedit.wsf /ar 0
Enable remote management
Configure-SMRemoting.exe -Enable
Enable-NetFirewallRule -DisplayGroup “Windows Remote Management”
Enable-NetFireWallRule -DisplayName “Windows Management Instrumentation (DCOM-In)”
Enable-NetFireWallRule -DisplayGroup “Remote Event Log Management”
Enable-NetFireWallRule -DisplayGroup “Remote Service Management”
Enable-NetFireWallRule -DisplayGroup “Remote Volume Management”
Enable-NetFireWallRule -DisplayGroup “Remote Scheduled Tasks Management”
Enable-NetFireWallRule -DisplayGroup “Windows Firewall Remote Management”
Enable-NetFirewallRule -DisplayGroup "Remote Administration"
Display current Remote Management settings
Configure-SMRemoting.exe -Get
Allow PowerShell Remoting
List available roles on Windows Server
List installed roles and features in Windows Server
Get-WindowsFeature | Where-Object {$_. installstate -eq "installed"} | ft Name,Installstate
Install role
Install-WindowsFeature DNS -IncludeManagementTools
List services
List stopped services
Get-Service | Where-Object {$_.status -eq “stopped”}
Restart service
Restart-Service -Name spooler
Manage processes
Task Manager taskmgr.exe
Get-Process cmd, wuaucl* | Select-Object ProcessName, StartTime, MainWindowTitle, Path, Company|ft
List physical disks status and health
Get-PhysicalDisk | Sort Size | FT FriendlyName, Size, MediaType, SpindleSpeed, HealthStatus, OperationalStatus -AutoSize
List free disk space
Get-WmiObject -Class Win32_LogicalDisk |
Select-Object -Property DeviceID, VolumeName, @{Label='FreeSpace (Gb)'; expression={($_.FreeSpace/1GB).ToString('F2')}},
@{Label='Total (Gb)'; expression={($_.Size/1GB).ToString('F2')}},
@{label='FreePercent'; expression={[Math]::Round(($_.freespace / $_.size) * 100, 2)}}|ft
List logs of last 10 boots
Get-EventLog system | where-object {$_.eventid -eq 6006} | select -last 10
List installed programs
Get-ItemProperty HKLM:\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\* | Select-Object DisplayName, DisplayVersion, Publisher, InstallDate | Format-Table -AutoSize
Download and extract archive file from an external website
Invoke-WebRequest https://servername/file.zip -outfile file.zip
Expand-Archive -path '.\file.zip' -DestinationPath C:\Users\Administrator\Documents\
Copy all files from a directory to a remote computer over the network
$session = New-PSSession -ComputerName REMOTEHOSTNAME
Copy-Item -Path "C:\Logs\*" -ToSession $session -Destination "C:\Logs\" -Recurse -Force
Force delete directory
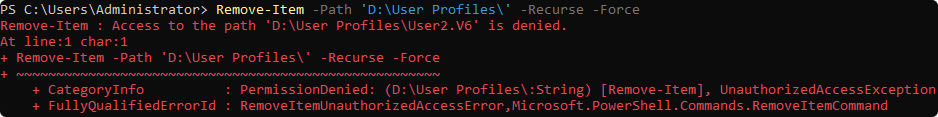
Take ownership
takeown /f 'D:\User Profiles /a /r /d y /skipsl
Change permissions
cacls 'D:\User Profiles' /e /t /g administrators:f
Delete directory
Remove-Item -Force -Recurse -Path 'D:\User Profiles'
List listening and established ports
Get-NetTCPConnection -State Listen,Established
List process names for the OwningProcess fields
Get-NetTCPConnection | Select-Object -Property *,@{'Name' = 'ProcessName';'Expression'={(Get-Process -Id $_.OwningProcess).Name}}
Check evaluation period
Extend evaluation period
Activate Windows Server
slmgr.vbs -ipk PRODUCTKEY
Activate your host on a KMS server
slmgr /skms kms.wildw1ng.local:1688
Windows 11
Proprietary graphical operating system developed and marketed by Microsoft

Bypass install restrictions
This PC can"t run Windows 11
Shift + F10
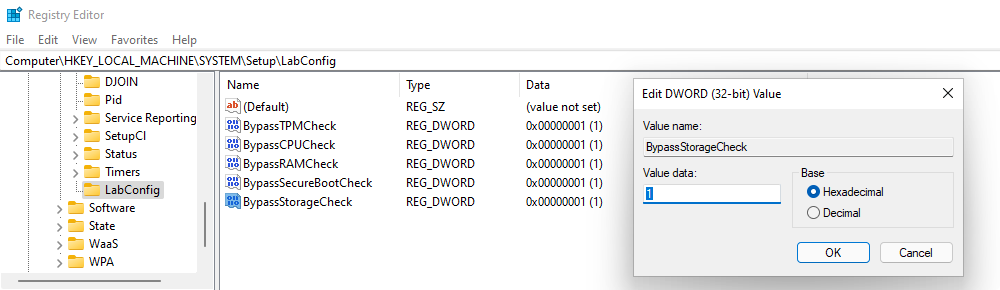
Computer\HKEY_LOCAL_MACHINE\SYSTEM\Setup\LabConfig
Create new key LabConfig
Create new dword32 entries
BypassTPMCheck 1
BypassCPUCheck 1
BypassRAMCheck 1
BypassSecureBootCheck 1
BypassStorageCheck 1
Bypass install restrictions with registry file
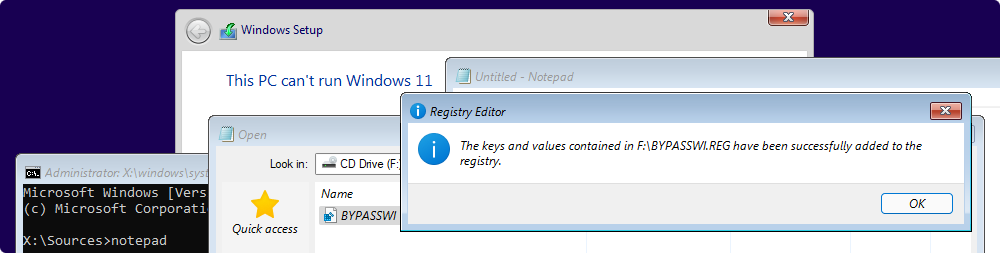
Download and mount bypass.iso prior installation.
SHIFT + F10 on “This PC can"t run Windows 11”.
Type notepad.
Click ‘File’ > ‘Open’.
Set ‘Files of type’ to All files.
Click on ‘This PC’ and navigate to the mounted drive.
Right click the *.reg file, click on ‘Merge’ and confirm.
Bypass network requirements during installation
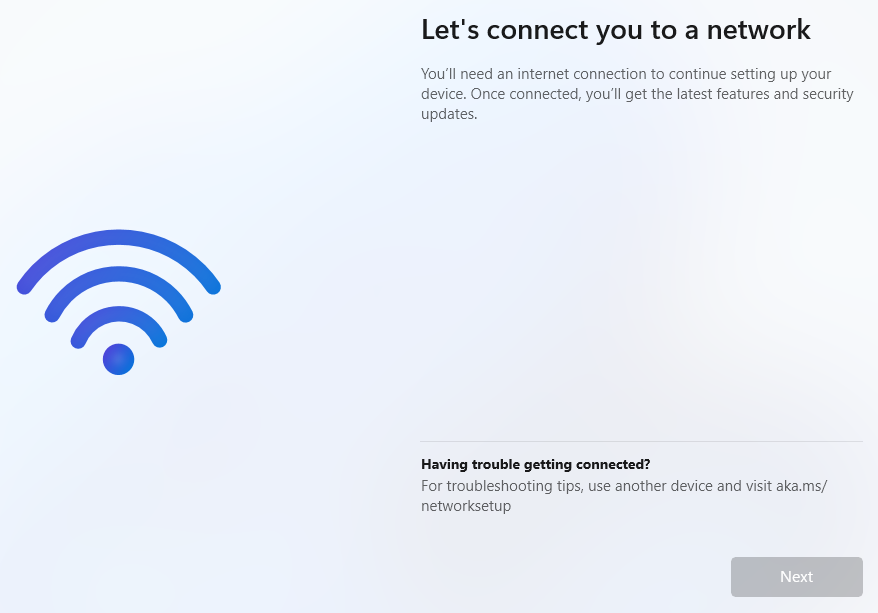 On the “Oops, you’ve lost internet connection” or “Let’s connect you to a network” page, use the Shift + F10 keyboard shortcut.
On the “Oops, you’ve lost internet connection” or “Let’s connect you to a network” page, use the Shift + F10 keyboard shortcut.
In Command Prompt, type the oobe\bypassnrocommand to bypass network requirements and press Enter.
The computer will restart automatically.
You will need to select the region and keyboard settings one more time to get to the network connection page.
Click the “I don’t have internet” option.
Click the “Continue with limited setup” option.
Post installation downloads
Set Active Directory domain server as DNS server
Join on-premises Active Directory domain
Get-WindowsCapability -Name RSAT* -Online | Add-WindowsCapability -Online
Open a new elevated PowerShell
Start-Process powershell -Verb runAs
Share a Linux host directory with a Windows guest
Enable shared memory
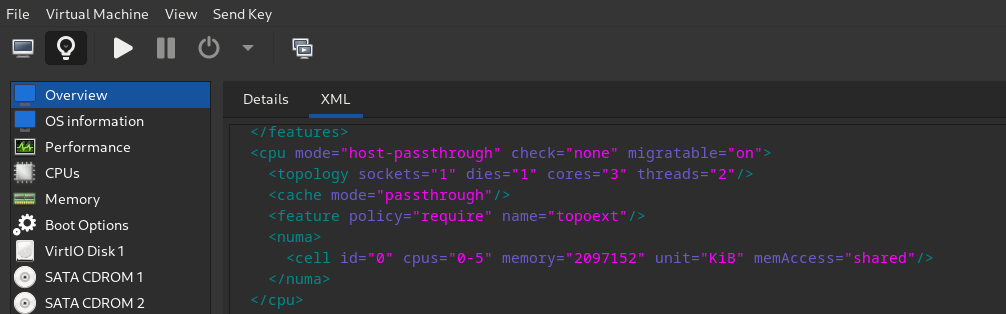
<memoryBacking>
<hugepages/>
<access mode="shared"/>
</memoryBacking>
<cpu>
<numa>
<cell id="0" cpus="0-5" memory="2097152" unit="KiB" memAccess="shared"/>
</numa>
</cpu>
Add a virtiofs filesystem passthrough
Add Hardware > Filesystem
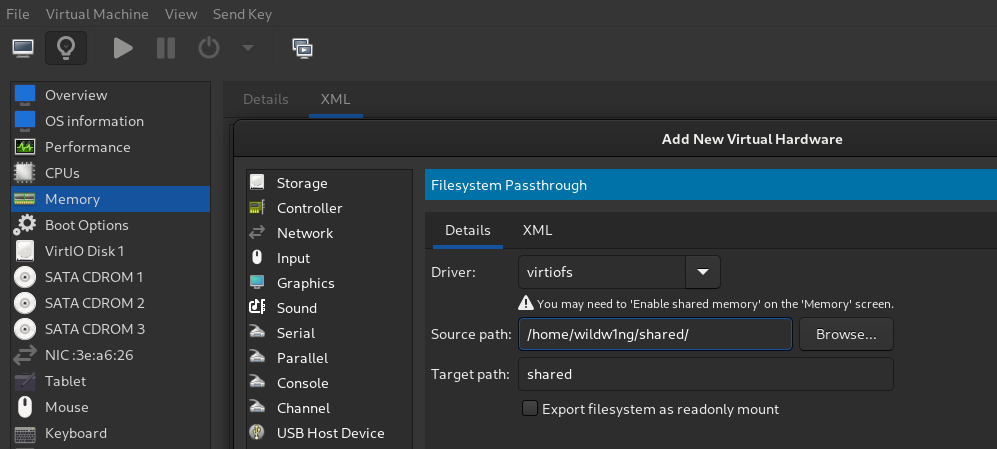
D:.\virtio-win-guest-tools.exe
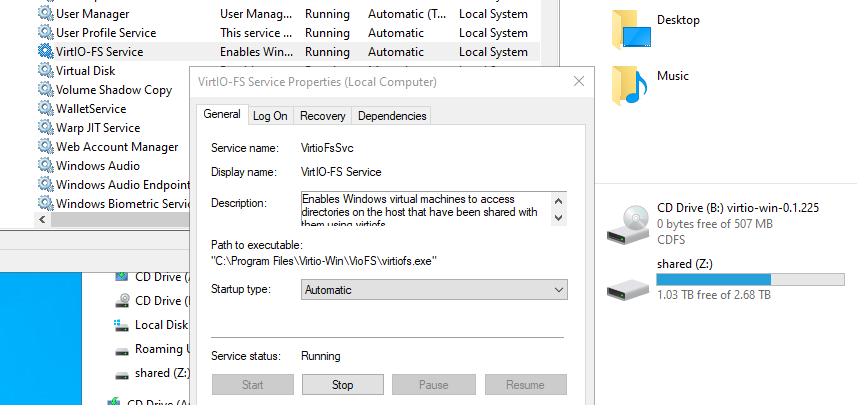
Install Windows File System Proxy on Windows guest (WinFsp)
Enable and start VirtioFsSvc service
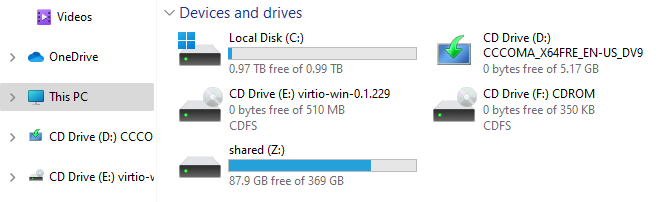
A new drive appeared and now we can read and write files in that directory from either the host or the guest.






 Profile path
Profile path 








 On the “Oops, you’ve lost internet connection” or “Let’s connect you to a network” page, use the Shift + F10 keyboard shortcut.
On the “Oops, you’ve lost internet connection” or “Let’s connect you to a network” page, use the Shift + F10 keyboard shortcut.




