Samba active directory
How to setup an active directory domain controller in Linux using Samba
Install packages
pacman -Syu krb5 python-dnspython openresolv samba bind
Rename machine
Windows NetBIOS names are limited to 15 characters (16-bytes)
/etc/hostname
arch-vm-addc
Setup network
Wired NAT adapter using a static IP
/etc/systemd/network/20-wired.network
[Match]
Name=enp1*
[Network]
Address=192.168.122.30/24
Gateway=192.168.122.1
DNS=127.0.0.1
chmod 644 /etc/systemd/network/20-wired.network
Second bridged wired adapter using DHCP for ssh access
/etc/systemd/network/21-wired.network
[Match]
Name=enp8*
[Network]
DHCP=yes
chmod 644 /etc/systemd/network/21-wired.network
Use local DNS server
Reconfigure resolvconf to use only localhost for DNS lookups.
/etc/resolv.conf.tail
# Samba configuration
search wildw1ng.local
nameserver 127.0.0.1
Set permissions
chmod 644 /etc/resolv.conf.tail
Regenerate the new file
resolvconf -u
System clock synchronization
Provisioning
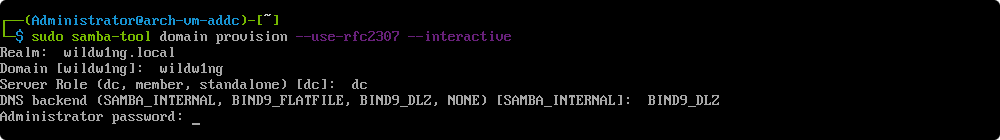 Performing basic directory configuration.
Performing basic directory configuration.
samba-tool domain provision --use-rfc2307 --interactive
–use-rfc2307
this argument adds POSIX attributes (UID/GID) to the AD Schema. This will be necessary if you intend to authenticate Linux, BSD, or macOS clients (including the local machine) in addition to Microsoft Windows.
–interactive
this parameter forces the provision script to run interactively.
BIND configuration
/etc/named.conf
// vim:set ts=4 sw=4 et:
acl local-networks {
127.0.0.0/8;
192.168.122.0/24;
};
options {
directory "/var/named";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
// Uncomment this line to enable IPv6 connections support
// listen-on-v6 { any; };
// Add this for no IPv4:
// listen-on { none; };
// Add any subnets or hosts you want to allow to the local-networks acl
allow-query { local-networks; };
allow-recursion { local-networks; };
allow-query-cache { local-networks; };
allow-transfer { none; };
allow-update { none; };
version none;
hostname none;
server-id none;
auth-nxdomain yes;
datasize default;
empty-zones-enable no;
tkey-gssapi-keytab "/var/lib/samba/private/dns.keytab";
// Uncomment if you wish to use ISP forwarders
// Google (8.8.8.8, 8.8.4.4, 2001:4860:4860::8888, and 2001:4860:4860::8844)
// OpenDNS (208.67.222.222, 208.67.220.220, 2620:0:ccc::2 and 2620:0:ccd::2)
// Appropriate values for subnets are specific to your network.
// forwarders { 8.8.8.8; 8.8.8.4; };
};
zone "localhost" IN {
type master;
file "localhost.zone";
};
zone "0.0.127.in-addr.arpa" IN {
type master;
file "127.0.0.zone";
};
zone "1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa" {
type master;
file "localhost.ip6.zone";
};
// Load AD integrated zones
dlz "AD DNS Zones" {
database "dlopen /usr/lib/samba/bind9/dlz_bind9_12.so";
};
//zone "example.org" IN {
// type slave;
// file "example.zone";
// masters {
// 192.168.1.100;
// };
// allow-query { any; };
// allow-transfer { any; };
//};
logging {
channel xfer-log {
file "/var/log/named.log";
print-category yes;
print-severity yes;
severity info;
};
category xfer-in { xfer-log; };
category xfer-out { xfer-log; };
category notify { xfer-log; };
};
chmod 644 /etc/named.conf
chgrp named /var/lib/samba/private/dns.keytab
chmod g+r /var/lib/samba/private/dns.keytab
touch /var/log/named.log
chown root:named /var/log/named.log
chmod 664 /var/log/named.log
Kerberos
Provisioning created a krb5.conf file for use with a Samba domain controller.
mv /etc/krb5.conf{,.default}
cp /var/lib/samba/private/krb5.conf /etc
/etc/krb5.conf
[libdefaults]
default_realm = WILDW1NG.LOCAL
dns_lookup_realm = false
dns_lookup_kdc = true
[realms]
WILDW1NG.LOCAL = {
default_domain = WILDW1NG.LOCAL
}
[domain_realm]
arch-vm-addc = WILDW1NG.LOCAL
chmod 644 /etc/krb5.conf
Samba
Enable printing and automatic sharing of all CUPS print queues
/etc/samba/smb.conf
[global]
rpc_server:spoolss = external
rpc_daemon:spoolssd = fork
printing = CUPS
[printers]
path = /var/spool/samba/
printable = yes
Share only specific print queues
/etc/samba/smb.conf
[global]
load printers = no
# Add and example print share
[HPDJ3050]
path = /var/spool/samba/
printable = yes
printer name = hpdj3050
Roaming profiles
chmod 0777 /profiles
Create samba share
/etc/samba/smb.conf
[profiles]
comment = User Profiles
path = /profiles
browseable = no
read only = no
csc policy = disable
vfs objects = acl_xattr
/etc/samba/smb.conf
# Global parameters
[global]
netbios name = ARCH-VM-ADDC
realm = WILDW1NG.LOCAL
server role = active directory domain controller
server services = s3fs, rpc, nbt, wrepl, ldap, cldap, kdc, drepl, winbindd, ntp_signd, kcc, dnsupdate
workgroup = WILDW1NG
idmap_ldb:use rfc2307 = yes
tls enabled = yes
tls keyfile = tls/key.pem
tls certfile = tls/cert.pem
tls cafile = tls/ca.pem
# rpc_server:spoolss = external
# rpc_daemon:spoolssd = fork
# printing = CUPS
[sysvol]
path = /var/lib/samba/sysvol
read only = No
[netlogon]
path = /var/lib/samba/sysvol/wildw1ng.local/scripts
read only = No
# [printers]
# path = /var/spool/samba
# printable = yes
[profiles]
comment = User Profiles
path = /profiles
browseable = no
read only = no
csc policy = disable
vfs objects = acl_xattr
chmod 644 /etc/samba/smb.conf
LDB utilities
/etc/profile.d/sambaldb.sh
export LDB_MODULES_PATH="${LDB_MODULES_PATH}:/usr/lib/samba/ldb"
chmod 0755 /etc/profile.d/sambaldb.sh
. /etc/profile.d/sambaldb.sh
Testing the installation
Verify tcp-based _ldap SRV record in the domain
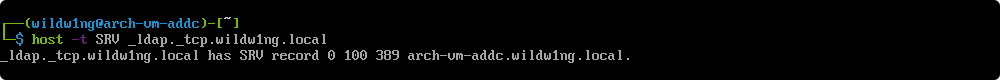
host -t SRV _ldap._tcp.wildw1ng.local
Verify udp-based _kerberos SRV resource record in the domain
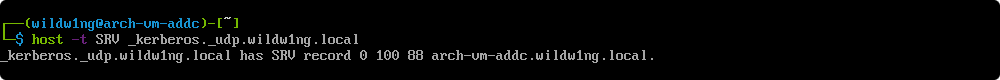
host -t SRV _kerberos._udp.wildw1ng.local
Verify A record of the domain controller

host -t A arch-vm-addc.wildw1ng.local
Verify NT password authentication
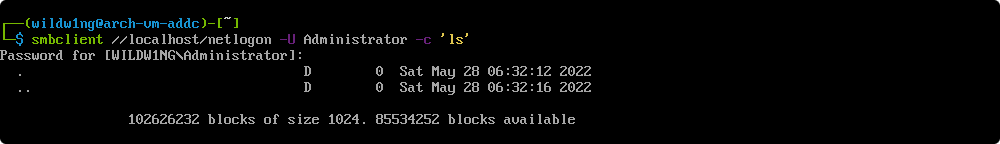
smbclient //localhost/netlogon -U Administrator -c 'ls'
Verify Kerberos is working as expected
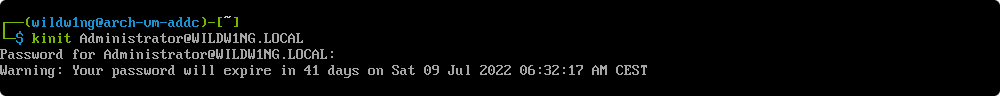
kinit Administrator@wildw1ng.local
If the “KDC reply did not match expectations while getting initial credentials” error occurs, check your /etc/krb5.conf.
Ensure that all Realm names are in upper case letters.
List cached Kerberos tickets
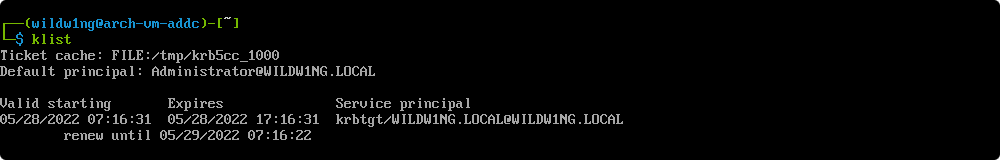
klist
Use smbclient with acquired ticket
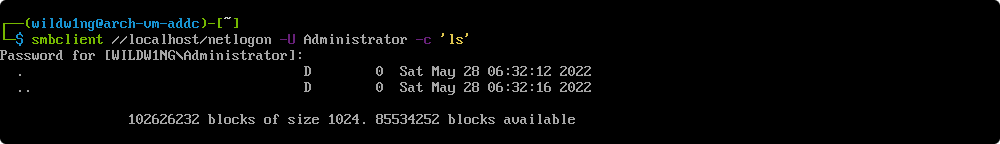
smbclient //arch-vm-addc/netlogon -k -c 'ls'
DNS reverse lookup
Create a reverse lookup zone for each subnet in your environment in DNS.
It is important that this is kept in Samba’s DNS as opposed to BIND to allow for dynamic updates by clients.
Use the first three octets of the subnet in reverse order (for example: 192.168.0.0/24 becomes 0.168.192)
Create a reverse lookup zone for each subnet
samba-tool dns zonecreate arch-vm-addc.wildw1ng.local 122.168.192.in-addr.arpa -U Administrator
Add a record for you server (if your server is multi-homed, add for each subnet). Add the fourth octet of the IP for the server.
samba-tool dns add arch-vm-addc.wildw1ng.local 122.168.192.in-addr.arpa 30 PTR arch-vm-addc.wildw1ng.local -U Administrator
Verify the lookup
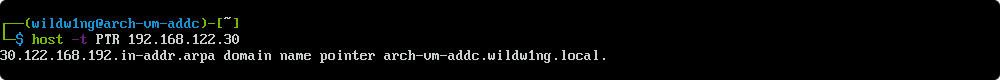
host -t PTR 192.168.122.30
Verify the file server
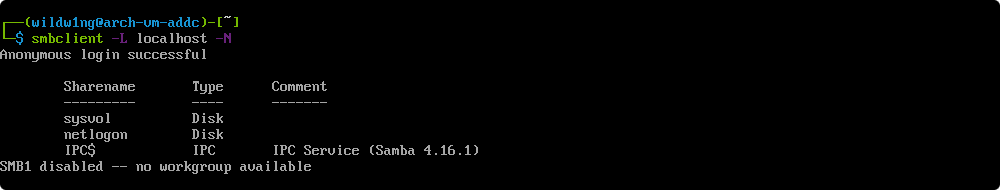
smbclient -L localhost -N
Enable services
systemctl enable named
systemctl enable samba
Manage roaming user profiles
Windows RSAT tools on Windows Client
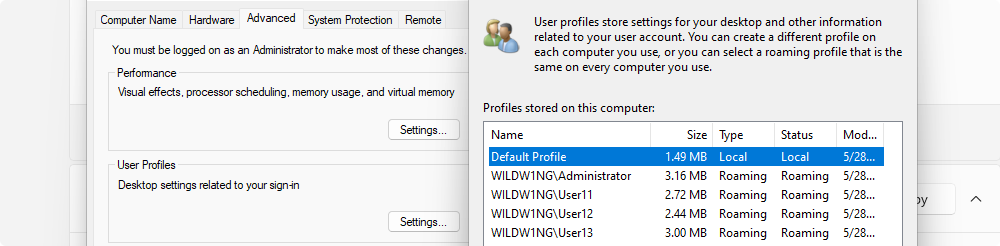
Use ‘Active Directory Users and Computers’ application on a Windows client to set the path to the user’s roaming profile and shared home directory.
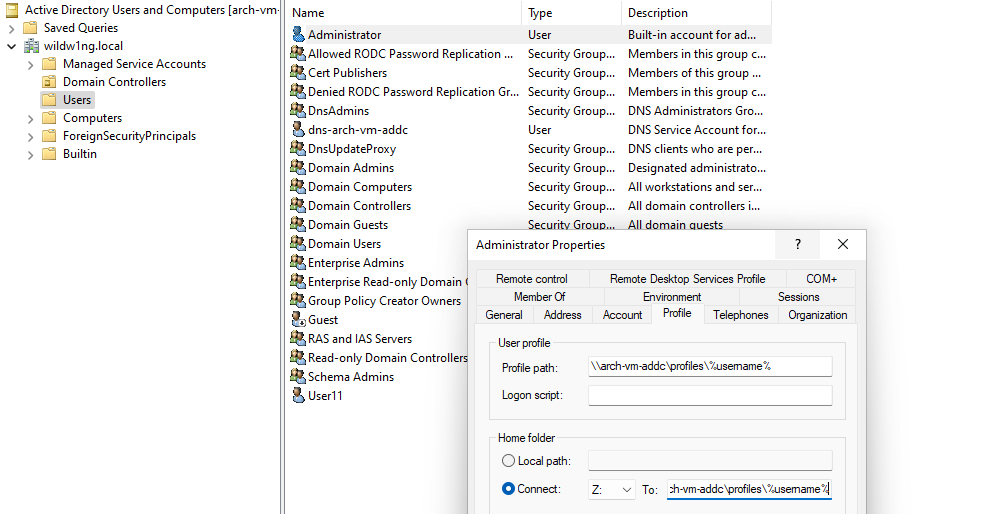
User profile \\arch-vm-addc\profiles\%username%
Home folder \\arch-vm-addc\shared\%username%
| Windows client OS sersion | Windows Server OS version | Profile suffix | Profile directory name |
|---|---|---|---|
| Windows NT 4.0 - Windows Vista | Windows NT Server 4.0 - Windows Server 2008 | none | user |
| Windows 7 | Windows Server 2008 R2 | V2 | user.V2 |
| Windows 8.0 - 8.1* | Windows Server 2012 - 2012 R2* | V3 | user.V3 |
| Windows 8.1* | Windows Server 2012 R2* | V4 | user.V4 |
| Windows 10 (1507 to 1511) | Windows Server 2016 | V5 | user.V5 |
| Windows 10 (1607 and later) | V6 | user.V6 |
Manage user profiles with Samba
samba-tool user list
samba-tool user create User11 Password11
--use-username-as-cn --surname="User"
--given-name="11" --initials=U11
--mail-address=User11@wildw1ng.local
--company="Company inc." --script-path=shire.bat
--profile-path=\\\\arch-vm\\profiles\\User11
--home-drive=Z
--home-directory=\\\\arch-vm\\shared\\User11
--job-title="Fancy title"
Manage group policies
 Samba policies can be found in the ‘Group Policy Management Editor’ within User or
Samba policies can be found in the ‘Group Policy Management Editor’ within User or
Computer Configuration > Policies > Administrative Templates > Samba
For Samba Domain Controllers, the Password and Kerberos settings are also applied, which are found in
Computer Configuration > Policies > OS Settings > Security Settings > Account Policy.